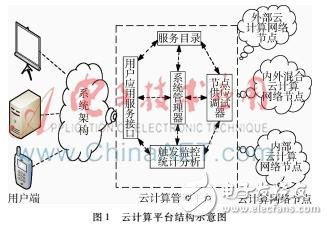
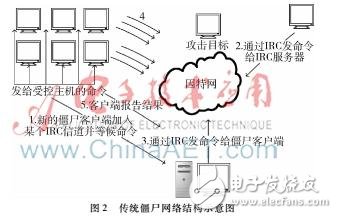
The botnet (BotCloud) in the cloud computing environment is a new botnet that transplants the traditional botnet to the cloud computing platform. Utilizing the advantages of the cloud makes botnet construction easier, attacks become more efficient, and detection becomes more difficult. This paper analyzes the similarity between the cloud computing platform and the traditional botnet structure, introduces the threat caused by BotCloud to the cloud environment platform, and analyzes the related detection technology of botnet in the cloud computing environment, which is the botnet in the future cloud computing environment. The test laid the theoretical foundation. In recent years, cloud technology has become an increasingly accepted technology and has become a fast-growing part of the information technology industry. It enables users to significantly reduce the cost of infrastructure and operations, and provides a fair charging system that ensures all of their services have There are many benefits such as scalability. Cloud technology not only provides these advantageous services to legitimate users, but also opens a door for malicious users who deploy attacks on third-party terminal devices connected to the Internet. Legitimate users resisting external attacks has always been a research hotspot of cloud technology security issues, but little attention has been paid to the possibility of transforming cloud platforms into platforms that can launch attacks. A botnet is one of the biggest beneficiaries of converting a cloud platform into attack support. A botnet that attacks through a cloud platform is called a botnet cloud network. The cloud computing platform has the characteristics of flexible service, resource pooling, on-demand service, service billable, and ubiquitous access. It can be seen from the structural diagrams of the cloud platform and the botnet of Figures 1 and 2 that the cloud computing platform is similar to many features of the traditional botnet: (1) Both are to aggregate the scattered resources to complete a task. The completion of the entire task depends on network traffic. The resources of the cloud computing platform and botnet are based on large network traffic and big data. . (2) The structure of both is based on one-to-many control. The centralized end of the botnet is the attacker, the attacker or the botnet control end, and the centralized end of the cloud platform is the cloud service provider. (3) Both make full use of computer resources. With the gradual maturity of public cloud and private cloud applications such as Google Cloud, Amazon Cloud, Apple Cloud, Baidu Cloud, the network has entered the cloud network era. At the same time, one of the cyber threats of botnets has entered this new era and has developed rapidly. In a cloud environment, botnets can be easily set up according to requirements, and it takes less time to build a very large-scale botnet, and the deployment cost is lower. Some illegal users have now demonstrated how to build a botnet cloud network in the cloud platform and try to launch various attacks. Users can rent a zombie cloud network for $9 an hour or $67 a day. The botnet is mainly used to launch distributed denial of service (DDoS) attacks, one of the biggest threats in network security. One of the experimental research is how to launch DDoS attacks in the cloud environment [7]. In addition, malicious behaviors such as spam, keyloggers, adware, spyware, click fraud, port scanning, etc. are more widely used in botnet cloud networks, causing greater economic losses to users. In 2009, the botnet launched an attack on Amazon's cloud-based EC2 (elastic computing cloud) service, causing internal service failures. In 2012, Microsoft also cracked two zeus botnet servers. These are just the tip of the iceberg where botnets are discovered, and there are still a large number of botnets that have not been discovered, especially in cloud environments. This paper analyzes the construction and structure of botnet cloud network, and on this basis, it better analyzes the influencing factors of botnet characteristics. Some achievements in traditional botnet detection research will also provide technical support for the detection and verification of botnet clouds. Traditional botnet detection mechanisms are based on behavioral characteristics, honeypot/honeynet technology, traffic clustering analysis, etc. These detection techniques play an ideal role in detecting botnets in traditional networks. However, due to the particularity of the cloud computing platform, these technologies cannot be directly used. Only by quickly and accurately detecting the botnet cloud network can we support the counter-attack and destruction of the botnet cloud network. When the infected end of the botnet cloud network launches an attack, there will be different metric characteristics from the traditional botnet. In 2014, HAMMI B analyzed the characteristics that might be generated when attacking the botnet cloud network from a system perspective [8]. A behavior detection method based on botnet cloud network is proposed. Due to the new features of cloud technology in botnet cloud networks, the use of traditional botnet behavior characteristics to detect botnet cloud networks has lost its role. Therefore, it is necessary to analyze the new characteristics of botnet cloud network behavior and then use feature similarity. Detect zombie cloud networks.
GPS Tracker, Locator for Precious Assets.
Features that already exist
âš« Tracking: It sends GPS (Location, speed) and sensors (if any) information to your application server with configurable report interval (moving or stationary).
âš« Geofence: It supports circle and polygon setting.
âš« Backup Battery (optional): With a backup battery (300mAh), the device sends a tamper message if the main power supply harness is disconnected.
âš« 3-Axis Accelerometer: With a built-in 3-axis accelerometer, the device can detect trip start/trip end, and to report harsh braking, harsh acceleration, and impact.
âš« Storing Message: The device stores up to hundreds of messages while there is no GSM signal.
âš« Low Voltage Detection (optional): Device switches to deep sleep mode if supply voltage drops below a threshold.
âš« Power Saving Mode: Device periodically wakes up and sleeps when vehicle engine is OFF.
âš« OTA (Over the Air): The device`s firmware can be upgraded via TCP.
âš« Waterproof Case: IPX65 waterproof
âš« Bluetooth-positioning: It will support bluetooth feature for positioning.
âš« Mileage: Reports trip start, trip end and the mileage.
âš« Drop Alarm: Using embedded light sensor to detect the drop/detach from the tracking object.
âš« Cell-ID Based Location: Device reports cell-ID based location information where
âš« Flexible battery selection
Other functions can be customized.
Asset GPS Trackers,Wireless GPS Trackers,4G asset GPS trackers,LTE asset GPS Trackers,Waterproof GPS Trackers eSky wireless Inc , https://www.eskygpsiot.com