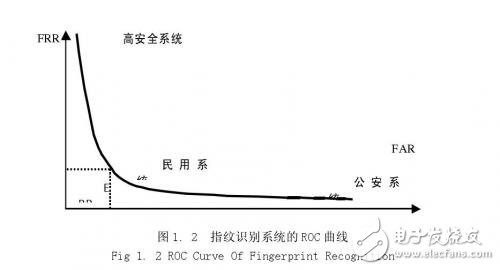
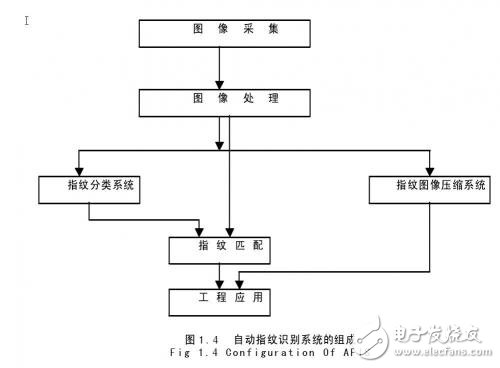
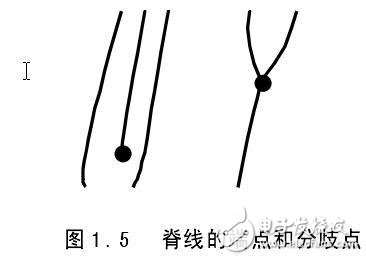
1.1 The drawbacks of traditional security technologies and the challenges they face Modern science and technology, represented by information technology, has greatly promoted the progress and development of modern society, providing a faster and more convenient means of communication for human beings. At the same time, it has brought a whole new importance to the managers of various countries and societies. Topic: How to verify the identity of each member of society in a timely and accurate manner. The traditional method of authentication is to verify that the person holds a valid supporting document or token. Essentially, this method verifies a certain "object" that the person holds, rather than verifying himself. As long as the validity of the "thing" is confirmed, the identity of the person holding the "object" is confirmed. This method of identifying people by "objects" clearly has the following vulnerabilities: 1. If a legitimate person loses the "object" (such as a password, key, etc.) that verifies his identity, the legitimate person himself will not be legally verified. 2. All kinds of forged documents, tokens and passwords are deciphered or stolen, and illegal people are legally verified. For example, some criminals enter confidential places to steal confidential information through forged documents. Another example is the attendance machine, which is convenient for enterprises to perform attendance management of employees, but the headache of the leaders is that people often falsify, punch cards on behalf of others, and take attendance instead of others. 3. If you lose the "object" that needs to be verified, such as the key, you will not only open the door, but also beware of the bad guy picking up your key to steal your family's wealth. Others use the key also have such problems. Many of the current computer systems, including many very confidential systems, use the "user ID + password" method for user identity authentication and access control. In fact, this scheme implies some problems. For example, passwords are easy to forget and are easily stolen by others. Moreover, if the user forgets his password, he cannot enter the system. The survey shows that the problem caused by forgetting the password has become one of the most common problems for IT vendors' after-sales service; passwords are stolen by others, which is even more terrible, because people with bad intentions may further steal company confidential data. It may steal other people's names to do improper things, and even withdraw huge deposits from others from banks and ATM terminals. In fact, the stealing of passwords is relatively easy. Others only need to pay attention to the keystrokes when you enter the password in front of the computer terminal to know your password. You can even guess your birthday, name, phone number or other information. The password, which is extremely unsafe. It is well known that highly confidential US military network networks (including the Pentagon and the Ministry of Defence) have been hacked more than once by hackers, and hackers have actually invaded the passwords of a legitimate user of these computer networks. Although current systems can prevent theft of passwords by requiring users to change their passwords at regular intervals, this approach not only increases the user's memory burden, but also does not solve the problem fundamentally. Table 1.1 shows the fraud losses caused by the United States in 1996 due to authentication. These problems indicate that traditional system security technologies that rely on tokens or passwords have faced severe challenges. Despite their simple and convenient integration, with the advent of the network society, e-commerce is becoming more and more popular, people want to use some more secure and reliable information to confirm that the person who deals with the other end of the network is his claim. That person. It is precisely because of the unreproducible advantages of human body features that it has become a hot spot in security technology research. 1.2 Introduction to Biometric System The so-called biometric identification is to use the physiological characteristics or behavioral actions of the human body to authenticate the identity of the person. Because these features are unique to each other, others cannot copy and replace, and using them to identify a person's identity is obviously much safer than using a password or token. Biometric requirements for verifying an individual's identity have the following properties. (1) The universality of the characteristics, that is, everyone must have, for example, only a part of the talents have birthmarks or scars, can not be used for a wide range of identification; (2) The uniqueness of the feature, that is, the characteristics of each person should be different from others; (3) The stability of the feature, that is, the feature or behavior should remain unchanged for a relatively long period of time, and the frequently changing feature is that the robustness of the identification system cannot be guaranteed; (4) Collectability, that is, whether these features or behaviors can be easily obtained and quantified. However, in practice, it is not enough to satisfy only the above four properties. The following issues need to be considered: (1) The overall performance of the system, that is to say, the use of this feature to identify the identity of the person, its speed, accuracy and robustness of the system can meet the specified index requirements; (2) Whether it is acceptable to adopt this biometric feature, whether it interferes with human privacy or harm to the human body, and whether it is convenient to operate, etc. In summary, for a practical biometric system, the following characteristics should be available: (1) Biometrics for identification can be accepted by people; (2) These biometrics can be easily obtained; (3) The recognition accuracy and speed of the system can meet the application needs; (4) The system should have sufficient adaptability for various deceptions. Figure 1.1 shows a block diagram of a generic biometric system. As can be seen from the figure, the biometric system is a pattern recognition system that identifies a person's identity by verifying the person's physiological characteristics or behavioral actions. Systemically, the system can be divided into two modules: registration and authentication. The function of the registration module is to store the biological characteristics of the human body in the identification system. At this stage, the biometric feature collector is first used to obtain the original information of the characteristics generated by the human body features, in order to reduce the storage amount of the biometric information, save the storage medium, and facilitate the subsequent Feature pattern matching process, these original information generally need to be further processed, compress the amount of information, extract the most effective feature information (generally called template template), and finally store the feature information in the user database according to the needs of different application projects. On the user IC card; the biometric authentication module is used to verify the identity of the person in the access control. At this stage, the collector is also required to acquire the biometrics of the human body, and then use a processing method similar to that in the registration module to describe the acquired information in a more compact form. The final matching sub-module uses the template in the template database to compare with the acquired compressed biometric information, and gives the judgment result. The biometric identification system shown in Figure 1.1 can be divided into two categories according to its application purpose, namely VerificaTIon and Identification (IdenTIficaTIon). Verification is the process of confirming identity by performing a one-to-one matching of the biometrics collected on site with a registered template. This one-on-one verification answers the question: Is he the person he claims to be? . Identification is to compare the biometrics collected in the field with the templates in the database, and find out the template that matches the characteristics of the site. This is also called "one-to-many matching" and is referred to as "1:N" alignment. Identifying this comparison method answers the question: Who is he? Verification and identification have their own characteristics in comparison algorithms and system design. For example, the verification system comparison speed is not as high as the recognition system, but it emphasizes the ease of use. In addition, in the identification system, classification technology is generally used to speed up the query or adopt a fast comparison algorithm. A system based on a token or password, due to artificial fraud or the negligence of the verifier, may cause verification errors, which are mainly manifested in misidentification. As a typical pattern recognition system, the biometric system has a certain degree of confidence. The result of this confidence has two kinds of misjudgments. One is to make the correct match as an error. Rejection (False Reject Rate, FRR), also known as rejection rate; the other is to accept the original mismatch as the correct (False Accept Rate, FAR), also known as the false positive rate. For an actual application system, if the system's rejection rate FRR is large, it will cause the user to input multiple times and cannot confirm its identity, which makes the user feel inconvenience, and thus causes distrust and disgust to the system; if the system is wrong A large FAR rate will reduce the security of the system and cause losses to legitimate users. In a biometric system, the system's rejection rate and misrecognition rate are a pair of contradictory parameters, and it is impossible to minimize the two parameters at the same time. A reduction in one parameter will inevitably lead to an increase in another parameter. Therefore, in practical application engineering, we can only adjust the parameters of the system according to different purposes to meet the needs of different purposes. For highly confidential access control, the rejection rate can be appropriately increased to minimize the false positive rate; conversely, the user of the general security level can appropriately reduce the rejection rate. For a biometric system, we generally use the ROC (Receiver OperaTIng Curve) curve to describe the overall performance of the system. Each point on the curve corresponds to the FRR and FAR of the system at a certain safety threshold. An example of the ROC curve is given in Figure 1.2. In practical applications, because the manufacturers and research institutions actually only give the best FRR and FAR, and these two parameters do not correspond to the same safety threshold, so a more scientific evaluation parameter --- error The rate (ERR) is widely used. The so-called equal error rate refers to the value of FRR and FAR when FRR is equal to FAR (as shown in Figure 1.2). Obviously, the smaller the ERR, the higher the overall security of the system. In addition, the matching speed of the system is also an important indicator of system performance, which is usually able to affect the ROC curve. Especially for the identification system, the speed is particularly important because of the "one-to-many" fingerprint matching. 1.3 Comparison of several biometric technologies Biometric technology either uses the physiological characteristics of the human body or uses human behavior. However, in terms of the accuracy of recognition, physiological characteristics are more reliable than behavioral actions. Because the physiological characteristics reflect the more essential part of the human body, it has better repeatability in the operation process, and it is not easy to imitate and copy. At present, biometric technologies widely used or hot research include: face recognition, fingerprint recognition, palm shape recognition, hand blood vessel recognition, iris recognition, retinal pattern recognition, facial thermal image recognition, human ear recognition, signature recognition and sound. Pattern recognition [36]. Among them, face, fingerprint, palm shape, hand blood vessel, iris, facial thermal image, human ear and retina graphics are physiological features, while signature and voiceprint are behavioral actions. Face recognition: It is the most intuitive and the most commonly used means of identity authentication. According to its application purpose, face recognition is divided into two modes: static recognition and dynamic recognition. The so-called static recognition is that the face image used for recognition is a static image, and the background and other external conditions are unchanged. In this case, the detection and segmentation of the face is very simple, and the distance between different images of the same face is relatively small, so the recognition becomes relatively easy. Dynamic face recognition refers to the recognition of faces in the context of complex changes. This type of recognition mode has many interference factors. At present, it is only in the laboratory research stage, and there are still many problems to be solved. Face recognition also mainly uses the positional relationship between various organs of the human face such as eyes, eyebrows, nose, mouth and chin. At present, effective algorithms used in face recognition include basic element analysis (PCA), linear discrimination analysis (LDA), singular point value decomposition (SVD), local feature analysis, and various neural network-based algorithms. The basic principle of facial thermal image recognition is such that when heat passes through the facial tissue, it is diverged by the skin, giving the subcutaneous blood system a unique facial signal. This signal can be acquired by an infrared camera, often referred to as a facial thermography. Compared to face recognition, facial thermal image recognition is difficult to counterfeit. Even in delicate surgery, it is difficult to rewire the blood vessel, changing its structure; and obtaining a facial thermal image does not depend on an external light source. Whether the current facial image is unique and stable remains to be verified. Fingerprints are uneven lines that are distributed on the surface of human fingers. The lines of different fingerprints are different in pattern, breakpoint and intersection, that is, the fingerprint is unique. By relying on this uniqueness, we can associate a person with his fingerprint, and by comparing his fingerprint with a pre-saved fingerprint, he can verify his true identity. Over the years, people have done a lot of research on fingerprint and fingerprint recognition. The uniqueness and stability of fingerprints have been strongly verified and widely used in judicial, public security and various security systems. Fingerprint recognition, as one of the first areas of pattern recognition, has developed extremely rapidly and has become synonymous with biometrics in many occasions. The palm shape recognition uses the geometric relationship of the palm to identify the person's identity. These dimensions mainly include the shape of the palm, the length and width of the finger, and the three-dimensional characteristics of the finger. The acquisition of the palm-shaped image can be done mechanically or optically. Palm-based identity authentication systems are now widely used around the world, such as the 1996 Atlanta Olympics and Disney theme parks. This identification technology is very simple and inexpensive, and can be easily embedded into existing application systems. The accuracy of recognition is also reliable under certain conditions, and people can accept it. Regarding this technology, its biggest disadvantage is that if it is used for identity authentication of large people, its recognition reliability will be greatly reduced, so it is generally only used to verify the system. In addition, the palm shape recognition has some problems. 1 The palm shape is also relatively easy to be counterfeited, and the physical size of the system itself is relatively large; 2 The stability of the palm shape is poor. The blood vessel distribution of the hand as a more stable biological feature can be used for identification. With an infrared camera, we can get a digital image of the blood vessels in the hand. The structure of the blood vessels in the hand is difficult to change by surgery, so others cannot imitate it. Based on the system of hand blood vessel recognition, the accuracy can basically meet the application requirements, and, in general, it is also more acceptable. The downside of this identification technique is that the uniqueness of the vascular features of the hand has not been reliably proven so far. The structure of human iris depends on the environment in which the embryo grows and develops, and it is unique and life-changing for everyone. Even the same person, his left and right eye iris is not the same. The iris is not associated with any other external environment and cannot be repaired by surgery. All these features make iris recognition the most reliable and reliable means of authentication. Experiments show that the recognition accuracy is even more simple than that of DNA. Iris recognition technology is relatively simple, but its recognition accuracy is quite high. Currently, there are two main reasons for restricting the application of iris recognition technology: 1. The collection of iris images requires the use of light to scan the human eye, making people feel uncomfortable; 2. The price of iris scanners is too high and it is still difficult to promote to the general civilian market. Retinal pattern recognition is similar to iris recognition and has high reliability, but because it has a stimulating effect on the human eye and the price has remained high, it has not been promoted in the application. The above describes several popular biometric identification technologies. Table 1.2 gives the uniqueness, stability, collectability, recognition accuracy, anti-counterfeiting performance and other parameters of these biometric identification technologies. From the table we can see that fingerprint recognition technology has advantages in terms of uniqueness, stability, recognition accuracy, anti-counterfeiting performance, etc. It is a biometric identification technology worthy of promotion. 1.4 fingerprint identification technology In this paper, our goal is to design an automated personal identity authentication system using fingerprint recognition technology. The reason why the fingerprint is used, from the above comparison, the fingerprint recognition technology has the following advantages: (1) Each person's fingerprints are unique and stable and do not change with age and physical health. (2) The effectiveness of fingerprint identification has been widely proved and recognized. (3) There are many kinds of fingerprint sampling equipments, and the price is low. In addition, a standard fingerprint sample library is available to facilitate the software development of the identification system. (4) A person's fingerprints are all different. In this way, multiple fingerprints can be conveniently used to form multiple passwords without increasing the design burden of the system, thereby improving the security of the system. (5) The template used in fingerprint recognition is not the original fingerprint image, but is composed of the detailed features extracted from the fingerprint image, so that the storage requirements of the fingerprint template library are reduced. In addition, the feature template also greatly reduces the burden of network transmission, and facilitates remote identification and network digital signature through fingerprints. Since the fingerprint recognition technology has the above advantages, an automatic fingerprint recognition system (AFIS) based on fingerprint recognition technology is generated under the demand of the judicial department. Figure 1.4 is a block diagram of the application of automatic fingerprint recognition. As can be seen from the figure, an automatic fingerprint identification application system needs to solve at least three key problems, namely, fingerprint image acquisition, fingerprint image processing, and fingerprint matching. In recent years, with the development of electronic integration technology, there are living fingerprint sensors that can directly acquire digital images. Some small-sized and easy-to-use live fingerprint image sensors have been widely used. The technologies used in these living fingerprint sensors are: 1. Optically attenuated total internal reflection (FTIR), 2. Ultrasonic reflection, 3. Holographic camera, 4. Thermal sensing technology, 5. Capacitance or deep electric field technology. In addition to the above-mentioned living body collection technology, these sensors also use automatic gain control technology, which can be used to obtain digital fingerprint images of different quality through software adjustment. For example, Veridicom's FPS200 capacitive fingerprint sensor can adjust the sensitivity of the capacitor discharge time and charge coupling time according to the feedback information during the fingerprint acquisition process, so that the image with unclear image (contrast difference) can be detected. To (such as where the finger is pressed lightly), and to increase the sensitivity of these pixels at the moment of capture. At the same time, it is also possible to control the image with the best capture effect according to the characteristics of the area of ​​the fingerprint image and the extreme gray scale. The processing technology of fingerprint image is the key technology in the automatic fingerprint identification system. The quality of the fingerprint image processing algorithm directly determines the reliability and speed of the fingerprint automatic recognition system. At present, the key technologies in the field of fingerprint image processing include direction segmentation algorithm, thinning algorithm, fingerprint image enhancement algorithm, and fingerprint image effective region extraction algorithm. Because each algorithm has its advantages and disadvantages, so far there has not been any excellent fingerprint image processing algorithms in the literature. The focus of this paper is to study these frequently occurring image processing algorithms and propose According to the characteristics of the fingerprint image, I propose my own image processing algorithm. Fingerprint matching mainly relies on the fingerprint detail feature (Minutiae). The common fingerprint detail features are mainly the following five types: endpoints, bifurcation points, bridges, intersections, and eye shapes. These features are not evenly distributed in the fingerprints. Their ratios are approximately 68.2%, 23.8%, and 3.7%. 3.2% and 1.1%. According to the FBI's suggestion, automatic fingerprint recognition systems generally only use the endpoints and divergent points of the ridge as the detailed features of the fingerprint, because several other features can be regarded as the synthesis of these two features. Figure 1.5 shows an example of these two features. The end point of the ridge line is the position where the ridge line ends, and the bifurcation point is the position where the ridge line branches. According to statistics, a complete fingerprint has about 60-80 detail features. Whether it is manual matching or machine matching, the process of fingerprint comparison can generally be divided into the following two steps: (1) correcting two fingerprint images according to the determined reference points, and searching for the detailed features of the two images; (2) Determine whether the two images are from the same fingerprint based on the pair of minutiae points on the match. At present, the commonly used automatic fingerprint identification system basically adopts a method of detail matching. There are several algorithms for matching based on detail points: Hough transform based method proposed by Stockman et al. transforms point pattern matching into peak detection in Hough space of conversion parameters. JPStarink and E.Backer describe points from the perspective of energy minimization. Matching the problem and using the simulated annealing method, Ratkovic of the Rand Institute proposed a more detailed fingerprint feature model. The model distinguishes between ten different fingerprint features. On this basis, JHLiu et al. used a method of superimposing a grid on a fingerprint and encoding the distribution of features to identify features. Both Sparrows and AKHrechak proposed fingerprint feature matching based on structural feature information, while DKIsenor and SGZaky used graphs to represent fingerprint features and used graph matching to match fingerprints. S. Sobajic et al. describe an algorithm that uses neural networks for detail point matching. These algorithms have high matching accuracy for the fingerprint image obtained by the ink method, and the FRR is lower than 10% in the case of 0.0001% FAR, but the image obtained by the crystal fingerprint sensor is less overlapped. The matching effect is not satisfactory. 1.5 The task of this paper Because traditional security technologies face the challenges of high technology and their security cannot meet the needs, people turn to the research of biometrics. Fingerprint recognition technology has certain advantages compared with several other biometric technologies, so it has become a research. Hotspots, but until now, there is no unified and effective standard algorithm for fingerprint image processing and recognition. Most companies also study some practical engineering application algorithms according to different application purposes. This paper attempts to design a better fingerprint image processing algorithm and automatic fingerprint recognition algorithm for Veridicom's FPS200 fingerprint sensor. The algorithm is oriented to the general small database civil system, and its target is to target about 200 fingerprint databases. The result is a misrecognition rate of 1*10-6, a rejection rate of less than 10%, and a 1:N alignment time of less than 3 seconds for a 100 fingerprint database. To achieve the above objectives, three main problems need to be solved: fingerprint image preprocessing, post-processing of fingerprint images, and application of fingerprint recognition technology. This paper aims to study the preprocessing and post-processing algorithms of fingerprint images, in order to find an image processing algorithm suitable for fingerprint identification systems in small civilian fields.
16 Port Usb Charger,16 Port Powered Usb Hub,200W High Poer Charger,Multiple Usb Desktop Chargers shenzhen ns-idae technology co.,ltd , https://www.szbestchargers.com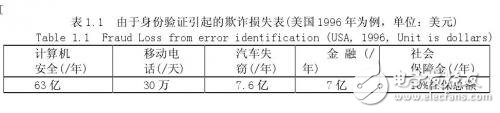






Research on Image Processing in Fingerprint Recognition--Basic Term Explanation
Function of 16 port USB charger
Each port of this 16 port USB charger can provide up to 5V, 2.4A power supply for charging battery intensive devices (such as iPad, iPhone, electronic devices, etc.). Compatible with all charging devices. At the same time, this mini version of the 16 port USB charger is light and portable. When you travel or go on business, it is correct to choose this one. With this 16 port USB charger, you can ensure that your device has sufficient power storage. No matter how many devices you charge, it will not affect the performance of your phone. It can also accelerate the charging speed of your device and protect your phone safely.