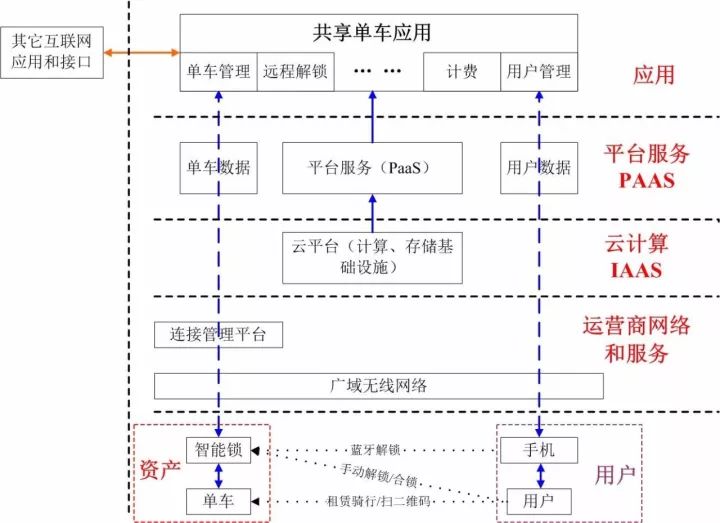
Shared bicycles have become one of the four new inventions in China and have been exported to many cities around the world. In my opinion, although the implementation of shared bicycles is not complicated, its essence is a typical "Internet of Things + Internet" application. One side of the application is the car (object), and the other side is the user (person), which provides the bicycle rental service to the user through the control of the cloud.

1. Cloud computing infrastructure platform
The cloud-sharing application for sharing bicycles is a large-scale two-way real-time application built on top of cloud computing. On the one hand, cloud computing can ensure the rapid deployment and high scalability of shared bicycle applications, on the other hand, it can cope with large-scale high-concurrency scenarios and meet the needs of millions of connections. (For example, Mobay's cloud service is built on Microsoft's Azure public cloud service platform)
2, data assets
Cloud applications need to collect, store and manage two types of key data: bicycle data (asset data of IoT characteristics: including bicycle communication connection status, lock status, usage record, etc.), bicycle data is passed by smart lock through communication module and SIM card , through the network of the telecom operator and the operator's IoT platform, uploading to the service platform of the shared bicycle; user data (user data of the Internet characteristics: in addition to basic user information, consumption records, user accounts and credit information, etc., User's behavior data: path and location information for the ride). As mentioned at the beginning of this article, shared bicycles are “Internet of Things + Internet†applications, so corporate assets (cycles) and user data are the core assets of shared bicycle companies.
3. Platform services
Since sharing bicycles involves massive IoT data and user data management, on the other hand, it is necessary to follow the user's needs for function development and optimization, so the platform service (PaaS) will be built first. Equipped with the platform service layer, on the one hand, it can enable applications to carry millions of high-concurrency data streams, and on the other hand, it can dynamically allocate resources and capabilities, and flexibly develop functions.
Therefore, Moby not only uses Microsoft's basic cloud service (Azure), but also uses Microsoft's platform services (PaaS), including "Azure-Iot" platform services, Dynamics, CRM, customer relationship management services, and machine-based learning. Predictive analysis capabilities, etc.
4, integrated application
The cloud shared bicycle application system integrates external Internet functions (such as payment, QR code application, electronic map, etc.), connects bicycles and users, and completes a complete rental service process (map search - two-dimensional scan code - User unlock - ride use - lock and return - payment settlement).
Throughout the leasing process, “intelligence (decision)†is actually implemented in the cloud. The cloud application dominates the interaction with the user and the switch that operates the smart lock, while the smart lock only performs user operations and cloud commands during the service process. In addition, cloud applications can also implement many extended applications, such as Internet marketing, electronic fences, bicycle reservation services, and so on.

From the Mobye 1st generation SMS unlocking and OFO 1 generation manual mechanical unlocking, to today's new functions such as Bluetooth unlocking, electronic fence, appointment, etc., the key functions of the smart lock and the basic functions have been gradually determined, each smart lock The difference is not big. At present, smart locks are basically composed of several types of modules such as control, communication, sensing, execution, and power supply.
The main module functions are as follows:
Control chip (microcontroller): The control center of the intelligent lock system, responsible for communication, car lock control and status information collection.
Mobile communication chip (Modem): A built-in telecom operator's Sim card, responsible for communicating with the cloud application background.
Bluetooth communication module: mainly used to connect the user's mobile phone and unlock it, and is also related to the implementation of the electronic fence.
GPS communication module: physical positioning function
The sensor of the car lock: senses the opening and closing state of the car lock, and reports the car lock state information to the control chip.
Actuator of the lock: The control chip opens and closes the lock by the actuator.
Buzzer: audible alarm for abnormal status
Power module: battery, charging module (chip), charging device (solar panel; motor and speed sensor, etc.)
The shared bicycle application is actually completed by the information transfer between the "cycling-cloud-user mobile phone", the most important of which is the process of unlocking the smart lock. At present, the latest "GPS positioning + Bluetooth" unlocking and returning mode has become more common.
Bluetooth mode unlock process:
1. The mobile phone first scans the two-dimensional code on the bicycle, and then initiates an unlocking request to the cloud (the request carries the ID information of the scanning code bicycle and the personal account information of the user). The cloud checks the user information and the bicycle information, and then sends the authorization information to the mobile phone. (Steps 1, 2)
2. The user transmits the unlocking instruction and the authorization information to the smart lock of the bicycle through the Bluetooth interface of the mobile phone, and the smart lock unlocks the authorization information, and notifies the mobile phone of the information of the successful unlocking. (Steps 3 and 4)
3. The mobile phone will reply the successful information to the cloud, and the cloud will start to charge the user. (Steps 5 and 6)
4. During the user's riding process, the bicycle and mobile APP will report their respective GPS positioning information to the cloud application. (Step 7)
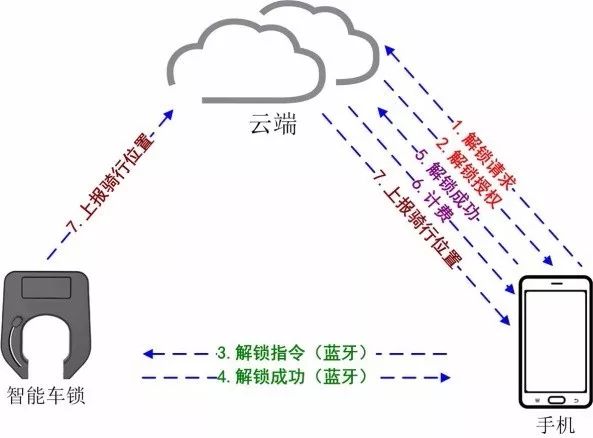
Bluetooth mode lock car, return process:
1. After the user locks the car, the smart phone notifies the mobile phone via Bluetooth: “Returning the car successfullyâ€. (step 1)
2. The mobile phone immediately informs the cloud that “the car is successfulâ€, and the cloud will send the fee settlement information to the mobile phone and the user. (Steps 2, 3)
3. The smart lock reports the location information after the user returns the car. (Step 4)

The use of Bluetooth to achieve the unlocking of the smart lock by the mobile phone can reduce the traffic (communication tariff) and power consumption of the smart lock. However, with Bluetooth, stability and compatibility are not guaranteed. Therefore, the traditional, relatively power-hungry unlocking method (manual password unlocking, GSM SMS or GPRS traffic unlocking) is often retained as an alternative.
SMS or traffic mode unlocking process (with GPS function):
1. The mobile phone first scans the QR code on the bicycle and then initiates an unlock request to the cloud. (step 1)
2. The cloud completes the information verification of the user and the bicycle, and sends the unlocking instruction to the bicycle smart lock, and the smart lock is turned on to reply “unlocked successfully†to the cloud. (Note: In the process of unlocking information for some shared bicycles, the smart lock will report the next unlocked password or key to the cloud) (steps 2, 3)
3. The cloud notifies the user of the phone and starts billing. (Step 4)
4. During the user's riding process, the bicycle and mobile APP will report their respective GPS positioning information to the cloud application. (Step 5)
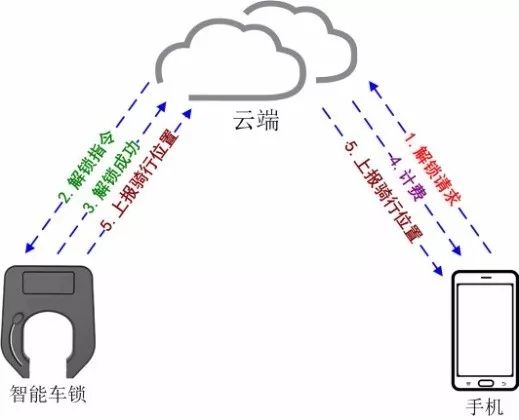
SMS or traffic mode lock and return process:
1. After the user locks the car, the cloud is notified by the smart lock: “Return the car successfullyâ€. (step 1)
2. The cloud immediately notifies the user's mobile phone and settles the fee. (Step 2)
3. The smart lock reports the location information after the user returns the car. (Step 3)

In practical applications, the closed unlocking process of each shared bicycle company will vary depending on the requirements and the configuration of the smart lock. From the iterative trend of smart locks, it can be seen that shared bicycle operators and smart lock suppliers are constantly working on optimizing solutions, on the one hand, pursuing the savings on traffic and power, and on the other hand, increasing the online rate and connection of bicycles. reliability.

On the whole, the application architecture of the shared bicycle "end-cloud-user" trinity is not complicated, but from the industry controversy and comment on all aspects of shared bicycles, it seems that the application of sharing bicycles is more than the pure Internet application. More complicated. In fact, the complexity is complicated by the management of the car. Because bicycles are no longer terminal devices (such as mobile phones, tablets) belonging to users, but the corporate assets of Moby and OFO.
Since bicycles are the most important asset, they need to be managed with care (in bicycle management, the main concern now is: power consumption, connection, part failure, location, frequency of use). There is a great positive correlation between the effective management of the bicycle and the user experience. The means and technology of the bicycle company's management of its assets (cars) will inevitably be iterated and improved.
Therefore, today's smart locks will be equipped with GPS positioning functions to facilitate the acquisition of bicycle positions and moving paths; smart locks can be equipped with Bluetooth unlocking function to reduce the communication traffic and connection uncertainty of the operator network. More energy saving;
Cycling companies follow up the NB-Iot network access solution promoted by telecom operators to reduce the power consumption of smart lock communication on the one hand, and increase the connection reliability on the other hand, which is more conducive to asset status tracking; research and development, testing, and trial operation. The electronic fence solution solves the problem of bicycle parking in public places in conjunction with municipal requirements; in addition, it develops more efficient and stable power supply methods, provides users with fault feedback pages, and so on.
In addition to "playing cars", bicycle companies also need to combine the big data analysis of user behavior to increase the frequency of bicycle use. For example, the user's tidal effect occurred in the morning and evening of the working day, that is, a large number of users “rushed†into the industrial park in the morning, and “returned†to the residential area in the evening to form a regular “migration†phenomenon.
Cycling companies need to consider how to dispatch bicycles to cater to the user's concentrated travel needs to improve asset (cycling) usage.

While shared bicycles have gradually become part of the daily lives of many people, they are clearly not perfect, and companies that share bicycles need to constantly polish their products and services. Of course, they are not alone.
Smart lock manufacturers will continue to participate in research and development and production of new locks. The iterative evolution of the operator network can further ensure that bicycles are always online. Cloud computing service companies will continuously optimize the system architecture and general capabilities of cloud applications, while various Internet companies Continue to provide supporting information services on demand, the services of upstream and downstream enterprises make shared bicycle companies only need to pay attention to their application logic and core assets, and focus on business thinking on the release of the value of cars and users.
As with shared bicycles, more shared products are also being developed and promoted in similar technologies and service environments. In the new intelligent product operation, in the new business cooperation, the relationship between the system and the system, between the objects and the objects is increased, the interactive data flow is widened, and the degree of automation and intelligence of the services are improved. The further extraction of the value of information in society has led to a more (connected) broad, (perceived) keen, (computing) intelligent world that is gradually being formed, and the world we don’t call it anything else, call it the Internet of Things. ".
Steel Picket For Fence,Steel Post,Steel Pile Driver, Star Picket,Fence Post,Steel Picket








